The regulatory compliance market is growing quickly, from $19.44 billion in 2023 to $21.16 billion in 2024, with an 8.8% annual growth rate. This growth is due to new legal frameworks and industry standards, stricter regulations, improved reporting rules, and greater public awareness.
How prepared is your organization to keep pace with these evolving demands? Perhaps your company is already implementing new policies, but are you using the right tools to stay secure and compliant?Discover how secure virtual data rooms can elevate your compliance. Trusted by thousands of companies worldwide, the solution helps businesses meet the highest security and regulatory standards!

What are audit trails in virtual data rooms?
Audit trails in VDRs are detailed records of actions taken within the platform. Simply put, they are a digital footprint that tracks how, when, and who accesses, shares, and modifies sensitive information.
Audit trails are especially essential for industries handling confidential or regulated data since they help teams ensure transparency, security, and regulatory compliance.
How do audit trails work?
When you upload documents to a data room, the platform automatically monitors and logs all user interactions. Specifically, audit trails capturing covers the following data:
- Access events – who accessed the document, when, and for how long.
- Edits and updates – details of changes made to confidential documents or folders.
- Downloads and shares – information on files that have been downloaded or shared, including recipient details.
- Failed attempts – instances of unauthorized or unsuccessful access attempts.
Using all this data, administrators can generate reports for review or regulatory purposes.
What are the core features of data room audit trails?
Commonly, audit trail functionality in virtual data rooms includes the following:
| Virtual data room feature | How they work |
| Document access and activity history | VDR audit trails offer granular visibility into data handling processes. In particular, they include user credentials, IP addresses, and device details so that a virtual data room admin can know who accesses the system. Additionally, they maintain a complete activity history, logging every action within a virtual data room as described in the section above. |
| Document version control | The software assigns unique identifiers to each file iteration, allowing users to compare, restore, or revert to prior versions. Also, virtual data rooms associate modifications with specific users for detailed scope and intent of edits. This functionality ensures that even as files evolve, the original and interim versions remain accessible for reference and accountability. |
| Time-stamped entries | Time-stamped entries allow administrators to reconstruct the sequence of events within the platform for detailed reporting. Furthermore, by associating every action with an exact time and date, audit trails spot irregularities, including access attempts during unusual hours or unexpected surges in activity. These insights help teams detect and address security threats. |
| Notifications for unusual or unauthorized access attempts | AI algorithms analyze user behaviour to identify deviations from the norm, including access attempts during unusual hours, bulk downloads, or actions inconsistent with typical activity patterns. When anomalies are identified, a data room sends real-time alerts to administrators to inform them of potential risks. These measures minimize vulnerability and enable teams to address threats immediately. |
| 👁️🗨️ Can you use an app data room to stay secure and compliant? |
Audit trails in VDRs are strategic tools for industries where accountability, compliance, and security are critical. In particular, they help ensure transparency and meet stringent regulatory requirements during sensitive finance transactions. Similarly, healthcare professionals can protect patient data and maintain compliance with privacy regulations like HIPAA compliance using audit trail data.
What is the importance of audit trails for compliance and security?
Healthcare, insurance, pharmaceuticals, energy, telecommunications, and banking are among the most regulated sectors governed by federal, state, and local regulations. For compliance, they need to protect sensitive documentation, control data access, and audit all activities related to data handling. Otherwise, companies risk legal and financial penalties, damage to their reputation, and loss of business due to non-compliance.
👁️🗨️ Real-life story!
In 2017, Heritage Valley Health System, operating across Pennsylvania, Ohio, and West Virginia, was hit by a NotPetya malware attack. The Office for Civil Rights investigation revealed multiple HIPAA Security Rule violations, including failure to conduct a risk analysis, lacking a contingency plan, and improper access controls for patient data.
Heritage Valley agreed to settle the case with a $950,000 fine and a corrective action plan, including risk assessments, updated policies, and staff training. This case highlights the growing threat of ransomware in healthcare and the importance of HIPAA compliance to protect sensitive patient data.
Heritage Valley’s case serves as a wake-up call for businesses to consider compliance and security measures to protect their operations and customers.
In short, prevention through compliance is far less costly than recovery after data breaches.
What are the compliance standards supported by audit trails?
Here is how audit trails fulfill the requirements of key compliance frameworks:
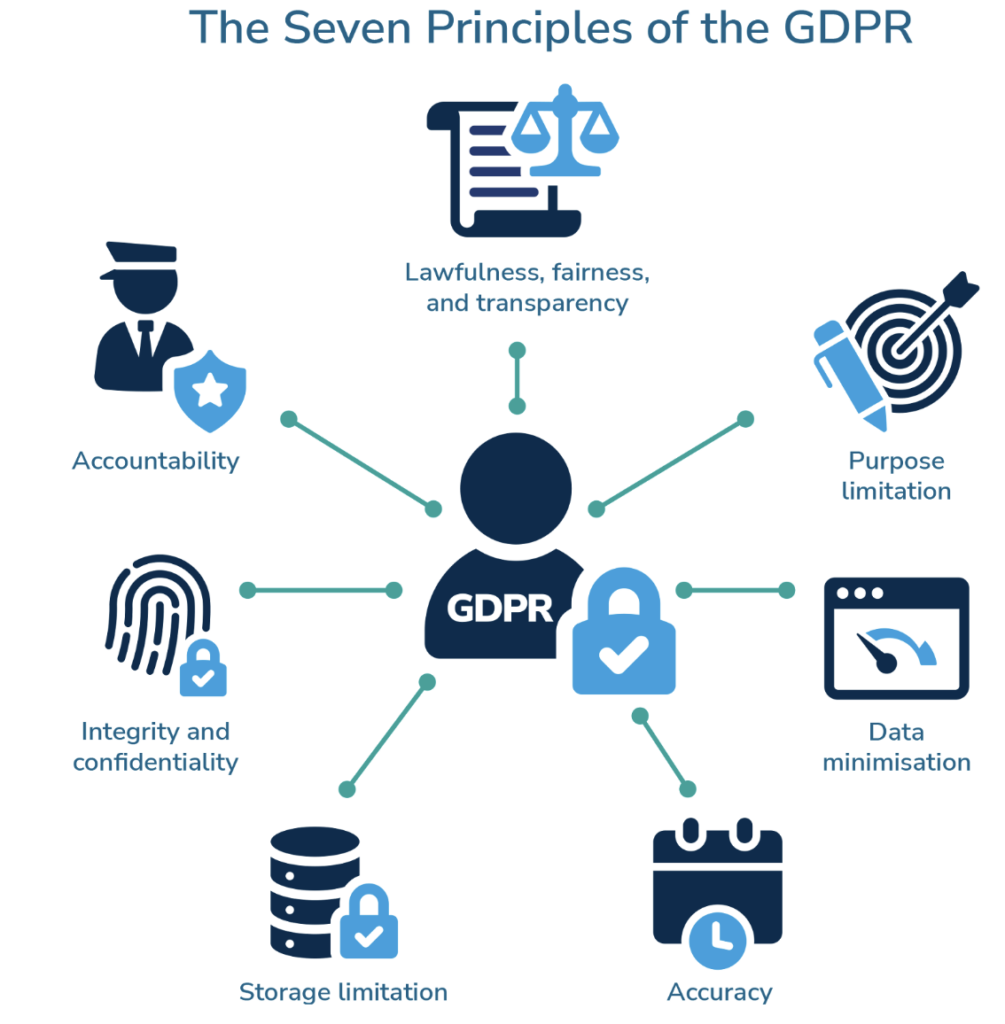
1. GDPR: Transparency and accountability
Under the GDPR compliance (General Data Protection Regulation), organizations must ensure transparency and accountability in handling personal data. Audit trails support this compliance by the following:
- Tracking data access and changes. Logs reveal who accessed or modified personal data, when, and why.
- Demonstrating accountability. Detailed logs can prove compliance during audits or investigations.
- Ensuring user rights. Audit trails confirm the timely handling of requests, such as data rectification or deletion, as required under GDPR Articles 15–21.
2. HIPAA: Patient information security
The Health Insurance Portability and Accountability Act (HIPAA) mandates stringent safeguards for the security and privacy of Protected Health Information (PHI). Audit trails support this compliance by the following:
- Monitoring PHI access. Audit logs show who viewed or altered patient data, preventing unauthorized use.
- Supporting risk management. Audit trails enable organizations to identify unusual activity or potential breaches.
- Ensuring audit readiness. HIPAA requires documentation of compliance efforts, and audit trails serve as evidence.
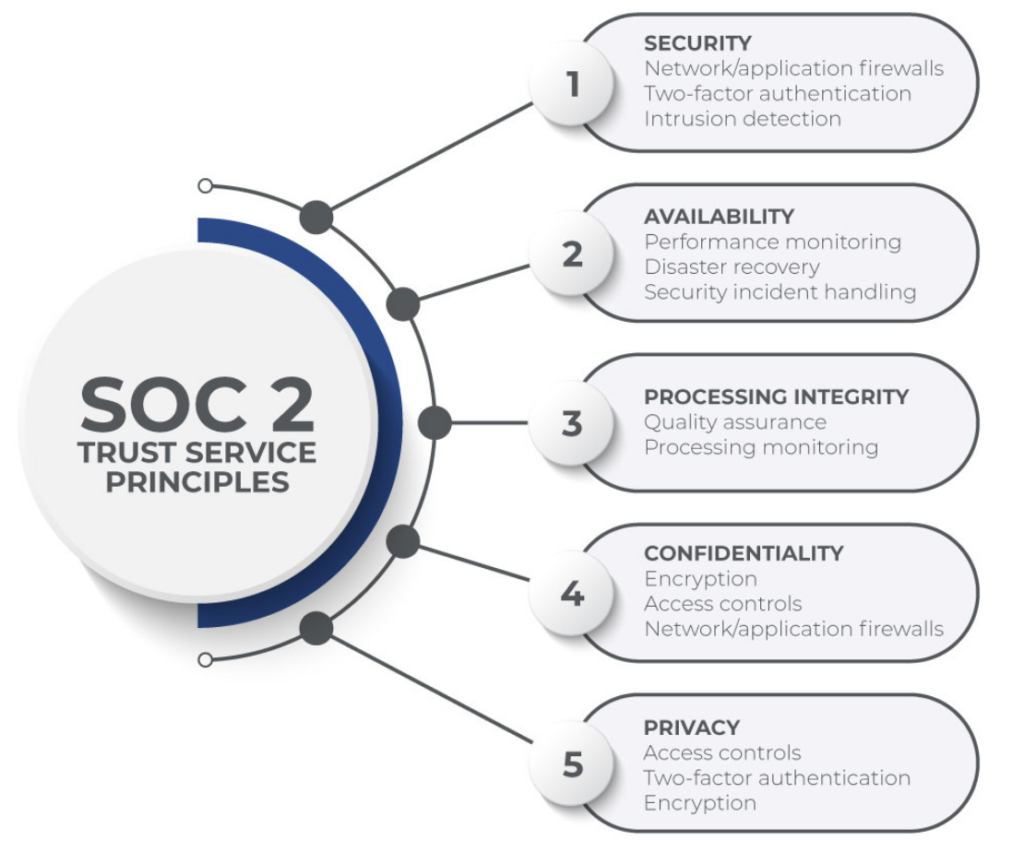
3. SOC 2: Secure data handling
The SOC 2 (Service Organization Control 2) standard focuses on data security, availability, processing integrity, confidentiality, and privacy. Audit trails support this compliance by the following:
- Tracking system activity. Logs record data access and processing details, ensuring confidentiality and security.
- Detecting anomalies. Continuous user activity logging enables real-time monitoring of suspicious activity to meet security incident response requirements.
- Simplified independent audits. Audit trails provide detailed visibility into system operations by tracking all user activity, data access, and changes, helping organizations demonstrate that their controls align with the SOC 2 Trust Service Criteria.
According to Investopedia, compliance costs an average of about $5.5 million, while the price of noncompliance is around $15 million, making it 2.7 times more expensive. Therefore, companies should allocate resources to tools that ensure compliance, improve data security, and streamline regulatory reporting processes.
More insights!
Compliance due diligence: Virtual data rooms vs physical data rooms
Compliance due diligence process evaluates whether a company adheres to legal, regulatory, and industry-specific standards before finalizing a transaction, such as a merger or acquisition. This involves reviewing policies, practices, and documentation related to data protection, labor laws, environmental regulations, and financial reporting. The goal is to identify compliance risks or liabilities that could impact the transaction.
Virtual data rooms streamline compliance due diligence by offering protected platforms where authorized parties can upload, organize, and access all relevant documents. Audit trails, user permissions, secure access controls, and encryption ensure sensitive information is protected and access is fully traceable. Unlike a physical data room, VDRs streamline efficient collaboration and provide tools to verify that all necessary compliance documentation is in place, making the process faster and more transparent.
Traditional data rooms require physical access to a secure location where sensitive documents are stored, making the due diligence process time-consuming and logistically challenging. Participants must travel to the site to review materials, often working within strict timeframes and under close supervision. This setup limits accessibility, increases administrative burdens, and makes tracking document interactions or ensuring real-time compliance monitoring nearly impossible.
What are the key benefits of using audit trails in a data room?
The software offers the following critical advantages for organizations handling sensitive or regulated information:
1. Strengthened data security through comprehensive tracking
Audit trails provide a detailed, time-stamped log of all activities within the platform. With this level of monitoring, VDR administrators can detect and mitigate suspicious or unauthorized activity instantly. Thus, they can ensure that only authorized users can access sensitive data.
2. Enhanced transparency for stakeholders
VDRs are used by internal teams and external stakeholders like clients, partners, and auditors. Audit trails improve transparency and establish trust by providing a clear record of document access and interactions. It ensures all parties can verify proper data handling, which is crucial in industries like law and finance.
3. Reliable audit log for internal reviews
Virtual data room users can use logs to review past actions, track document changes, and ensure compliance with internal protocols. This reliable and detailed record can be referenced to resolve disputes, conduct regular security audits, or demonstrate due diligence in case of an inquiry or audit by regulators.
4. Instant identification of unauthorized access or unusual behavior
If someone tries to access documents they are not supposed to, or if there is a pattern of suspicious activity, the audit trail provides the documentation needed to act quickly. This immediate visibility allows for faster resolution of security incidents, minimizing potential harm to the organization.
While virtual data rooms offer crucial benefits, businesses must still consider a few challenges. Check them to protect your company!
What are the common pitfalls when using audit trails?
Keep in mind the following pitfalls:
1. Over-reliance on logging without active monitoring
Some businesses rely solely on audit trails for activity and document tracking but fail to monitor them in real time. Without continuous oversight, suspicious or unauthorized activity can go unnoticed for long periods, escalating security breaches or compliance issues.
Best practices:
- Enable VDR alerts for unauthorized activities
- Assign a team to monitor audit trails regularly
- Use data room real-time monitoring tools
2. Overlooking unusual activity patterns
Audit trails generate vast amounts of sensitive data, making it easy to miss subtle but important signs of unusual behavior. For example, multiple failed login attempts, unusual access times, or large file downloads might seem insignificant unless closely analyzed. Failing to detect these patterns can make organizations vulnerable to threats, including data theft or unauthorized access.
Best practices:
- Leverage virtual data room analytics for anomaly detection
- Set thresholds for activities like downloads or access times
- Regularly review audit trails for patterns
3. Inconsistent log management
Without proper configuration, audit trails may not capture all relevant activities, or some events may be logged inaccurately. Incomplete or inconsistent trails can create challenges when conducting internal reviews or responding to regulatory audits, compromising compliance efforts.
Best practices:
- Customize a virtual data room to log all critical actions
- Audit the logs for accuracy and completeness
- Enable tools that provide summarized reports to simplify log reviews
4. Ignoring user privacy concerns
In some cases, excessive logging of user actions can raise concerns about privacy and data protection. Therefore, businesses must ensure that audit trails comply with privacy laws and do not unnecessarily invade users’ privacy, especially when dealing with sensitive or personal data.
Best practices:
- Limit logging to necessary actions
- Inform users about tracking policies
- Allow users to view what is logged about their actions to build trust
5. Failure to regularly review and update audit trail policies
If a company doesn’t adapt to new threats, technologies, or regulatory changes, they can leave audit trails ineffective in identifying current risks. Therefore, teams must ensure their audit policies remain relevant and up-to-date to maintain optimal security and compliance.
Best practices:
- Schedule regular reviews of audit trail policies
- Incorporate feedback from security and compliance teams
- Use simulated scenarios, such as security drills, to test the effectiveness of current policies
Applying these practices can significantly reduce common audit trail pitfalls. However, choosing a reliable virtual data room provider is equally important!
Checklist: What are the best virtual data room providers for compliance and security?
When choosing a platform, consider the following:
Compliance features
- Adherence to relevant regulations (e.g., GDPR, HIPAA, SOC 2, ISO 27001)
- Customizable user permissions
- Advanced reporting features
- Detailed audit trails
- Retention policies for maintaining data per regulatory requirements
2. Advanced security features
- End-to-end encryption for secure document sharing and storage
- Multi-factor authentication
- Watermarking and access expiration
- IP-based access restrictions and activity alerts
- Regular updates of the platform that address security vulnerabilities
3. User access and control
- Granular control over document permissions
- Real-time monitoring of user activity
- Easy-to-use dashboards for managing security settings
- Single sign-on integration for user authentication
4. Data integrity and backup
- Redundancy with regular backups to prevent data loss
- Tamper-proof logging for audit trails
- Data recovery options in case of system failures
5. Vendor reputation
- A proven track record with positive client reviews and testimonials
- Expertise in supporting compliance-heavy industries
- Case studies or references relevant to your sector
6. Support and training
- 24/7 customer support for urgent issues.
- Detailed user guides and compliance training resources
- Onboarding support for configuring virtual data room security settings
7. Cost vs. value
- Transparent pricing with no hidden fees
- Scalable solutions to grow with your needs.
8. Additional considerations
- AI tools for detecting unusual activity patterns
- Integrations with existing compliance and security software
- Customizable reports to demonstrate compliance to regulators
Use this checklist to evaluate and compare the best virtual data room providers!
Conclusion
Compliance builds trust, prevents penalties, and ensures smooth operations. By incorporating reliable tools for audit trails, your business can tackle compliance challenges head-on and avoid costly penalties. So, partner with a trusted virtual data room provider to simplify compliance and protect your organization’s future!



