Jun 01 ‘22
11 min read
The best way to share sensitive information is to use online services that keep business files private and secure with end-to-end encryption. It’s all rather obvious, isn’t it? However, while there are many ways to save and share files securely online, some may not be safe enough for businesses across industries, which is obvious from the visual below.
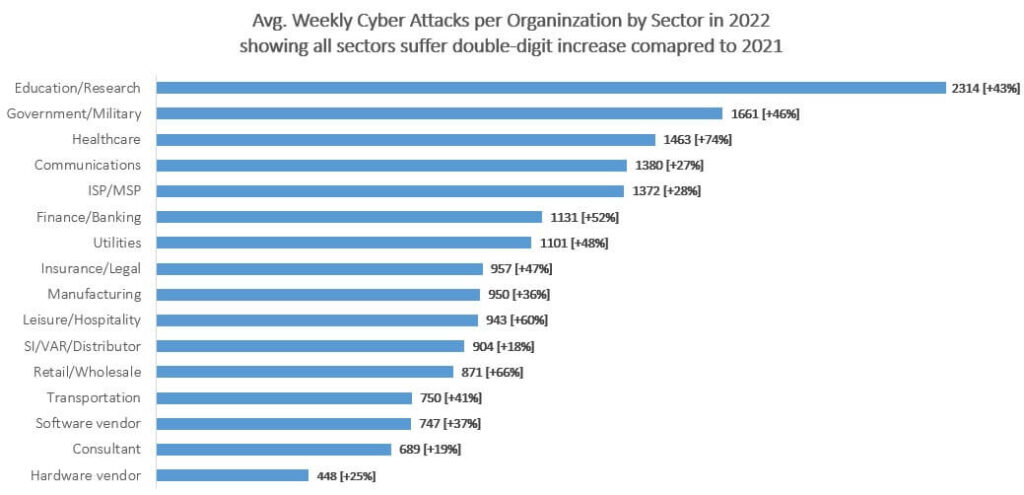
So, what is the best way to share sensitive information? What are the traditional and modern methods of sharing business files? What should be considered when choosing between secure file-sharing platforms? Dive into our guide and find the answers!
What is sensitive information?
Sensitive information is any form of data that requires high protection due to its confidentiality or personal nature. In business, it includes but is not limited to personal, financial, and business-critical data.
- Personal information is any data identifying an individual, such as their name, address, phone number, social security number, birth date, credit card information, genetic and biometric data, sexual orientation, and other confidential information. Businesses typically collect and process personal information for specific purposes, such as employment or providing goods and services.
- Financial information in business refers to data and reports that relate to a company’s economic performance. This information helps analyze a business’s financial well-being and make informed decisions about its operations and investments. Examples of financial information include balance sheets, income statements, cash flow statements, and financial ratios, which provide detailed information about a company’s assets, liabilities, revenue, expenses, and profitability.
- Business-critical data refers to information vital for decision-making, planning, and managing operations. It can vary based on the industry and business needs. For instance, these documents may include customer data such as demographics, buying habits, and customer preferences. All this provides insights into customer behaviour and influences marketing strategies and product development.
Based on our experience, data security is only as strong as its weakest sharing point. So, you should take care of the file-sharing solution and data protection strategies you use.

Traditional methods of sharing sensitive information and their limitations
Although traditional data-sharing methods are becoming obsolete, they are still widely used. This is why it is crucial to carefully evaluate the security risks associated with each traditional solution to protect sensitive information.
Email is a popular file sharing solution as it allows for swift and easy transfer. This long-standing technology is user-friendly, especially for non-technical users, as no additional software is required.
One of the most significant limitations of email is the file size limit. Most email providers set a maximum file size to be attached to an email. If the file size exceeds this limit, you can’t send it, which can be a significant problem when sharing large files such as videos or presentations.
Another question – is it safe to send important documents via email? No. The lack of advanced encryption methods makes the transfer of confidential documents vulnerable to interception and unauthorized access.
Moreover, emails can be lost or delayed in transit, and there is no way to ensure that the recipient has received the intended message or attachment.
Physical documents
Sharing files by courier involves sending them by mail. A courier service ships a USB or physical document and delivers it to the destination by air or ground. The limitations of courier services are that they can be slow and expensive, and there is no guarantee that your documents will be delivered safely. Furthermore, it may be challenging to track records if they are lost or stolen during delivery.
So, sending files by courier is like mailing a fragile package that may take a long time to arrive and could get damaged or lost along the way.
Fax
Nowadays, the use of fax machines has declined due to the outdated method of sending and receiving paper faxes. However, some industries, such as banks, real estate, insurance, healthcare, and legal firms, still rely on it.
As for downsides, faxing can be costly as it requires a landline phone number, which is uncommon in most modern offices. In addition, high maintenance costs are involved, including ink, toner, and paper. Moreover, the recipient of your documents must also have access to a fax machine, which is often not the case.
Evidently, most business leaders prefer better alternatives for streamlined and secure file sharing. In this way, they avoid serious data breach consequences, including a loss of customer trust, legal penalties, and significant financial losses.
In fact, financial losses can amount to millions, as seen in the largest data breaches worldwide.
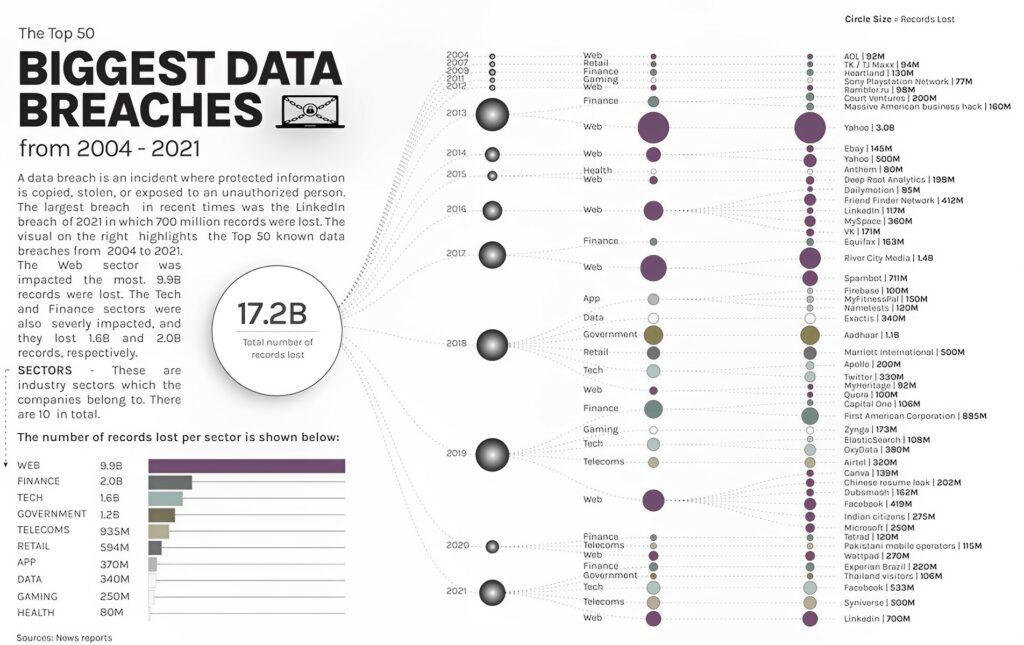
Modern ways of sharing sensitive information securely
Since traditional methods cannot always securely send sensitive information, those prioritizing security opt for online file-sharing solutions. Based on our observations, the most secure cloud services are as follows:
Secure virtual data room encryption
This secure file-sharing platform knows how to protect sensitive documents, satisfy security protocols, and build trust with your clients and partners.
In the tips below, we will elaborate on the data rooms features.
- Safety through granular permission settings: A majority of virtual data rooms have granular permission settings. These define the user who has access to sensitive files. You can attach viewing permission to individuals but also to groups. You can even change authorization at any given time, which gives you full control over who sees what. Moreover, audit logs are a reliable source of information on activities in the secure data room.
- Remote shred security: To increase document security, you can also establish the time in which a file will be available in the virtual data room. You can define for how long it can be accessed, and you can restrict access to those files even after someone downloads them. Combined with the granular permission you ensure double safety with your confidential data.
- Certification compliance: Compliance with international standards is key to the data room software provider’s cybersecurity strategy. Thus, they prove the reliability of implemented data privacy and integrity controls. The most advanced certifications in the industry are ISO/IEC 27001:2013, SOC 1 or 2, GDPR, and HIPAA.
- Visual protection: The most secure data room providers who know how to share sensitive information include innovative features for superior protection of sensitive information during complex business transactions. For example, the fence view prevents unauthorized viewing, screen capture, and printing. Secure spreadsheet viewer, in turn, makes working with data in Excel safe, enabling you to customize access levels. And watermarks make each document easily traceable, eliminating an unidentified data security breach.
- Time and IP access restriction: With these advanced security features, admins restrict logins from specific IP addresses. In addition, they can set the session duration and the access expiration date. As a result, companies can control access to critical documents inside and deal with external parties.
If you compare virtual data rooms, you will notice the last two options are not available from all data room vendors but only from market leaders who know how to share sensitive information securely.
With granular permissions and remote shred, virtual data rooms simplify take your security control to the next level, designating who can access sensitive data at any given moment.
Microsoft Word PDF encryption
One of the most popular word processors in the world, Microsoft Word, has a built-in encryption feature. To use it on PDF documents follow these steps:
- When you are done editing your Word document, enter the File tab and click Export.
- Pick Create PDF/XPS to craft a PDF document.
- Select the Options button in the Save window, and then press Encrypt the document with a password. Confirm by clicking the OK button.
- Put in your desired password, and click the OK.
Microsoft Word DOCX encryption
If you would like to encrypt a DOCX document, you can also do that in Microsoft Word. Simply follow these steps:
- Select the document you want to encrypt and open it in Microsoft Word.
- Click on the File tab, then select Info and Protect Document.
- Pick Encrypt with Password.
- Write your password, and confirm encryption by clicking OK.
PDF encryption with Adobe Acrobat
Apart from encrypting your PDF in Microsoft Word, you can also encrypt with Adobe Acrobat software. Open your PDF document in Acrobat and:
- Go to Tools, select Protect, then Encrypt, and finally Encrypt with Password.
- Select Yes, if a pop-up with a security change confirmation appears.
- Choose Require a Password to Open the Document, and put in your password.
- Choose the version of Adobe Acrobat that would support that document.
- Select Encrypt All Document Contents.
- Press OK, verify your password when asked, and press OK once more.
File encryption in Microsoft Excel
Another popular program from Microsoft has its own encryption method. To encrypt your file in Microsoft Excel, follow these steps:
- Go to File, and select Info.
- Pick Protect Workbook and then select Encrypt with Password.
- Write your desired password, and then press OK.
- Verify your password in the Re-enter Password box, and press OK to confirm.
There are a variety of ways to securely share files. But if you want to ensure sensitive data is safe, it’s important to take additional security measures. By using Microsoft Word, Adobe Acrobat, or even Microsoft Excel you can create some level of security with encryption, but by investing in the capabilities of virtual data rooms you can be certain your documents won’t be accessible by third parties. It is what makes virtual data rooms one of the most secure file sharing platforms.
You may also like: virtual data room vs. Google Drive
Factors to consider when choosing a method to share sensitive information
Our findings indicate that the key factors to consider when choosing among secure file sharing services are security, accessibility, confidentiality, traceability, and compatibility.
| Security |
Security is the most critical factor to consider when sharing sensitive information — the method of sharing must be secure enough to protect the information from unauthorized access. End-to-end encryption, a dedicated user account, password protected, data leak prevention mechanisms, and two-factor authentication are some measures you should look for. |
| Accessibility |
The method of sharing should allow the recipient to access the information quickly. If the recipient has to jump through hoops or have specific technical knowledge to access the information, they are unlikely to want to spend time on it. |
| Confidentiality |
The recipient should be the only person who can gain access to the information. Using a method that allows multiple recipients increases the risk of data falling into the wrong hands. |
| Traceability |
If the information falls into the wrong hands, it should be possible to trace who accessed it and when. It will help identify the leak’s source and take appropriate action. |
| Compatibility |
The method of sharing should be compatible with the recipient’s system. Data exchange may fail if the recipient cannot access the information due to compatibility issues. |
Considering these best practices for handling sensitive information, you can ensure that the information is shared with the right people. Check out top VDR providers and choose what best fits your needs!
Key takeaways
- Personal, financial, business-critical, and other types of information require strong privacy protection. If this information is revealed, it could present a significant security risk to individuals and organizations.
- Modern data-sharing methods are considered the best ways to share sensitive information. They use encryption and other privacy tools for data sharing, which makes it harder for malicious actors to access data.
- When choosing file-sharing software, consider security, accessibility, confidentiality, traceability, and compatibility.
Category
Security & risksFAQ
The three most secure encryption techniques are RSA with 2048-bit (Rivest-Shamir-Adleman), AES with 256-bit keys (the Advanced Encryption Standard), and Triple DES with 56-bit keys (Triple Data Encryption Algorithm).
To protect sensitive data you can enable data encryption, employ data obfuscation to replace your original files with fictional ones, set-up multi-factor authentication, create data backups, and implement stronger network security using antivirus software, intrusion detection systems, virtual private networks, etc.
The best way to share sensitive documents is to use a proven platform that is powered by state-of-the-art security mechanisms and complies with data protection standards. As an option, you can consider a virtual data room, the functions of which guarantee unmatched security of data sharing.
To store sensitive documents securely, you can use virtual data rooms, Sync, Egnyte, Microsoft Drive, or Dropbox. To make the right decision, check what security features a particular tool includes and how much data the storage can keep and protect.

